The Internet of Things, or IoT — it has quietly become the backbone of how modern enterprises operate. From smart factories and connected vehicles to intelligent healthcare systems and energy-efficient offices, IoT is everywhere. In 2026, the number of connected devices is expected to cross 30 billion, each collecting, sharing, and acting on data in real time. This web of interlinked devices is helping businesses make faster decisions, improve efficiency, and create more personalized customer experiences.
But with this convenience comes a new challenge—security. Each connected device, no matter how small, acts as a digital entry point. A single weak link can expose an entire network to hackers. In the last few years, there have been incidents where smart cameras, industrial sensors, and even connected thermostats were exploited to launch large-scale cyberattacks. These events have shown that IoT security isn’t just a technical concern anymore—it’s a boardroom discussion that directly affects business continuity, trust, and reputation.
As enterprises expand their digital operations, the lack of proper IoT security frameworks can lead to data breaches, operational shutdowns, or regulatory penalties. That’s why 2026 marks a significant shift—companies are now expected to follow established IoT security standards and compliance frameworks to protect their systems and customers. These frameworks provide structured guidance on how devices should be built, connected, and maintained securely. They ensure that organizations don’t just react to threats but build protection right from the start.
In this blog, we’ll explore the most reliable IoT security frameworks and standards every enterprise should adopt in 2026. You’ll understand what these standards mean, how they differ, and why they’re crucial for building safe, scalable IoT ecosystems. We’ll also touch on regional regulations, emerging trends, and practical steps enterprises can take to stay compliant and secure in a world where everything—and everyone—is connected.
Understanding IoT Security in 2026
IoT security in 2026 goes far beyond protecting devices—it’s about safeguarding entire ecosystems of data, connectivity, and automation. At its core, IoT security refers to the methods and practices used to protect connected devices, networks, and data from cyber threats. From smart sensors in factories to medical monitoring systems and connected vehicles, every device that communicates online must be secured against misuse or intrusion. The goal is simple: ensure confidentiality, integrity, and availability of the data flowing through billions of interconnected devices.
What makes IoT security more complex than traditional IT security is its scale and diversity. Unlike a standard IT system that deals with computers and servers, IoT environments involve devices with varying hardware, software, and communication protocols. Many of these devices have limited computing power and can’t handle advanced encryption or real-time security monitoring. Additionally, they often operate in open, distributed environments—factories, transportation systems, or homes—making them more vulnerable to physical tampering or network-based attacks.
By 2026, enterprises face a new generation of cyber risks shaped by advanced technologies. AI-driven attacks are among the biggest concerns, as hackers now use artificial intelligence to identify vulnerabilities faster than ever. Supply chain risks have also grown, with attackers targeting third-party components or firmware to compromise entire systems. Other common threats include device spoofing (where fake devices mimic real ones to access networks) and firmware exploitation, which targets outdated or unpatched device software. With thousands of devices connecting to a single enterprise network, a single weak link can open the door to massive disruptions.
Emerging technologies like edge computing, 5G-enabled IoT, and digital twins are reshaping the landscape—and introducing new security challenges. Edge computing brings data processing closer to devices, reducing latency but increasing the number of endpoints that need protection. 5G networks enable faster and more reliable connectivity, but also expand the attack surface. Meanwhile, digital twins—virtual replicas of physical systems—rely heavily on accurate, secure data streams; a single data breach could corrupt both the real and digital systems simultaneously.
To tackle these challenges, organizations are increasingly embracing Zero Trust IoT Architecture. This approach is built on the principle of “never trust, always verify.” Instead of assuming devices or users within a network are safe, Zero Trust continuously validates every connection, action, and identity. This model fits perfectly with IoT ecosystems where devices frequently communicate across networks, vendors, and platforms.
In short, IoT Security Frameworks emphasize
- proactive protection,
- continuous verification, and
- integrated compliance.
As businesses become more connected and rely heavily on data, following proper IoT security rules and meeting cybersecurity requirements are no longer choices—they’re necessary steps to build a safe, reliable, and trusted digital future.
Why IoT Security Frameworks and Standards Matter
As IoT continues to power the digital backbone of enterprises in 2026, the importance of IoT Security Frameworks cannot be overstated. These frameworks serve as structured blueprints that guide how organizations should secure their connected devices, data, and networks. With thousands of devices communicating simultaneously, having a consistent and well-defined security approach helps eliminate confusion, reduce vulnerabilities, and ensure every system follows the same security principles.
Enterprise IoT Security protocols bring reliability and structure to complex IoT deployments. They define best practices for everything from data encryption and device authentication to network monitoring and incident response. By following these standards, enterprises can maintain consistency across different departments, vendors, and device types—creating a uniform line of defense. More importantly, they simplify compliance with global Cybersecurity Compliance for IoT regulations, ensuring businesses meet both legal and ethical responsibilities when handling data.
To understand their role better, it’s useful to distinguish between frameworks, standards, and guidelines:
- Frameworks provide the overall structure or strategy for implementing security (like NIST or ISO frameworks).
- Standards define specific, measurable requirements that must be followed to ensure compliance.
- Guidelines offer recommended practices that can be adapted based on an organization’s needs.
Together, they create a strong foundation for secure and scalable IoT ecosystems.
The benefits of following these frameworks go beyond security. They help mitigate risks, enhance customer trust, and ensure interoperability between different IoT systems. For global enterprises, this consistency builds confidence among partners and clients, showing that the company values data protection as much as innovation.
Neglecting standardized security, on the other hand, can lead to serious consequences. In recent years, poorly secured IoT devices have been exploited to launch large-scale attacks, such as DDoS incidents that took down major websites and disrupted supply chains. These breaches highlight a painful truth—without proper frameworks, even one vulnerable device can compromise an entire network.
By 2026, enterprises that adopt robust IoT Security Frameworks and integrate Zero Trust IoT Architecture are better equipped to protect data integrity, ensure compliance, and maintain operational resilience in an increasingly connected world.
Top Global IoT Security Frameworks and Standards in 2026
By 2026, the world of IoT has matured from early experimentation to large-scale enterprise adoption. Businesses across industries—manufacturing, healthcare, logistics, finance, and energy—depend on connected devices for automation and data-driven insights. However, this vast ecosystem also demands strong security foundations. To meet global expectations, organizations now rely on well-established IoT Security Frameworks, designed to ensure data privacy, device integrity, and regulatory compliance. Below are the most recognized Enterprise IoT Security Standards and frameworks that every enterprise must follow to build a secure IoT ecosystem.
4.1. ISO/IEC 27001 and ISO/IEC 27030 (IoT Security Management Standards)
Overview of ISO/IEC 27001 and its IoT relevance
ISO/IEC 27001 has long been the gold standard for information security management systems (ISMS). It defines how enterprises can establish, implement, maintain, and continuously improve their security processes. In the context of IoT, ISO/IEC 27001 ensures that device data, user information, and communication channels are managed securely throughout their lifecycle. It brings structure and accountability to enterprise IoT deployments by aligning risk management practices with global best practices.
Introduction to ISO/IEC 27030 (latest IoT-specific guidelines)
Recognizing the growing importance of IoT, ISO introduced ISO/IEC 27030, a framework focused on IoT-specific risks. Released in its updated form in 2026, ISO 27030 addresses the unique challenges of connected devices—such as lightweight encryption, firmware management, and secure data exchange between devices and cloud systems. It acts as an extension to ISO 27001, helping enterprises apply proven cybersecurity principles to IoT ecosystems.
Implementation benefits and best practices for enterprises in 2026
For organizations, adopting ISO/IEC 27001 and 27030 provides clear benefits—stronger governance, improved compliance, and reduced breach risks. Best practices include defining clear roles for IoT data handling, using encryption at both device and network levels, and maintaining audit trails for data access. Many organizations incorporate a Zero Trust framework for IoT into these standards to authenticate and monitor each device connection in real time.
4.2. NIST IoT Cybersecurity Framework (CSF 2.0)
Overview of the National Institute of Standards and Technology (NIST) Cybersecurity Framework
The NIST Cybersecurity Framework (CSF) remains one of the most influential security models globally. Initially developed for critical infrastructure, it now serves as a universal guide for managing cybersecurity risks across sectors. Its modular approach helps organizations assess current security maturity and plan for future resilience.
Updates and modifications for IoT in 2026 (CSF 2.0 release)
The 2026 release of NIST CSF 2.0 introduced expanded guidance specific to IoT devices. It focuses on securing device identity, ensuring supply chain transparency, and protecting communication integrity between sensors and cloud services. It also emphasizes IoT compliance requirements, helping organizations meet both federal and international data protection standards.
Key functions: Identify, Protect, Detect, Respond, Recover
NIST’s framework is structured around five key functions:
- Identify: Understand assets, risks, and potential threats within IoT ecosystems.
- Protect: Implement access control, encryption, and firmware integrity measures.
- Detect: Monitor network activity for unusual patterns or breaches.
- Respond: Define incident response plans tailored to IoT-specific threats.
- Recover: Restore services, update firmware, and prevent recurrence after attacks.
How enterprises can align with NIST IoT guidelines
To align with NIST CSF 2.0, enterprises should maintain an updated inventory of IoT devices, segment networks, apply identity-based authentication, and automate patch management. Integrating these controls with Zero Trust IoT Architecture ensures constant verification of every device action.
4.3. ETSI EN 303 645 (Consumer IoT Security Standard)
Background and global adoption status in 2026
Developed by the European Telecommunications Standards Institute (ETSI), EN 303 645 sets baseline security requirements for consumer IoT devices. By 2026, its influence extends far beyond Europe, with governments and enterprises worldwide adopting it as a benchmark for device manufacturers and service providers.
Major security provisions
ETSI EN 303 645 outlines essential controls such as:
- No default or weak passwords.
- Mandatory software and firmware updates.
- Secure storage and transmission of personal data.
- Transparency around data usage.
- Reporting mechanisms for security vulnerabilities.
Application in enterprise IoT ecosystems
While originally designed for consumer devices, its principles now apply to enterprise IoT systems too. Following ETSI EN 303 645 helps organizations ensure that every device connecting to their network meets a basic security hygiene standard—an essential step in broader IoT Security Frameworks 2026 compliance.
4.4. IoT Security Foundation (IoTSF) Compliance Framework
Overview of the IoTSF framework and its growing importance
The IoT Security Foundation (IoTSF) has emerged as one of the leading global organizations promoting best practices for IoT security. Its framework provides end-to-end guidance for securing IoT products—from design and development to deployment and lifecycle management.
How IoTSF supports manufacturers, developers, and enterprises
IoTSF’s framework emphasizes collaboration among stakeholders—manufacturers, software developers, and enterprise users—to ensure that security is built in, not bolted on. It supports a certification program where compliant organizations can showcase adherence to IoT security best practices, helping them gain trust in competitive markets.
Key principles and certification process
Key principles include secure design, risk assessment, patch management, and clear incident reporting. The IoTSF certification process involves audits, vulnerability testing, and documentation reviews to ensure products meet international Cybersecurity Compliance for IoT benchmarks.
4.5. Cloud Security Alliance (CSA) IoT Controls Framework
Importance of cloud-integrated IoT security in 2026
In 2026, as more IoT devices rely on cloud services for data analytics and remote control, cloud security becomes inseparable from IoT protection. The Cloud Security Alliance (CSA) IoT Controls Framework provides a structured approach to securing device-to-cloud communication and managing cloud-based risks.
How CSA standards ensure device-to-cloud protection
CSA focuses on access management, data encryption, and secure APIs between IoT platforms and cloud environments. It addresses shared responsibility—defining which security aspects fall under the enterprise and which under cloud providers.
Integration with multi-cloud and hybrid environments
Modern enterprises operate across hybrid and multi-cloud infrastructures. The CSA IoT Controls Framework ensures that IoT data remains protected regardless of where it resides. By combining CSA controls with a Zero Trust security model for IoT, businesses can ensure consistent protection across all layers, from edge devices to cloud environments.
4.6. OWASP IoT Security Verification Standard (ISVS)
OWASP’s contribution to IoT device and application security
The Open Web Application Security Project (OWASP) is widely respected for its role in defining secure software practices. Its IoT Security Verification Standard (ISVS) provides a detailed checklist for evaluating IoT device and software security.
The latest ISVS version and its focus on device lifecycle protection
The 2026 version of ISVS expands beyond testing to include continuous monitoring. It emphasizes secure device provisioning, communication encryption, and safe firmware updates—critical for protecting IoT devices through their entire lifecycle.
Best practices for developers and enterprises
Enterprises use ISVS to set security benchmarks for vendors and developers. Regular code reviews, penetration testing, and automated vulnerability scans are recommended best practices. Combining OWASP ISVS with IoT Security Frameworks ensures a proactive defense against evolving IoT threats.
4.7. IEC 62443 (Industrial IoT and OT Security)
Importance in manufacturing, energy, and smart city sectors
The IEC 62443 framework focuses on securing Industrial Control Systems (ICS) and Industrial IoT (IIoT) environments. In 2026, it’s widely adopted across manufacturing, oil and gas, utilities, and smart cities—sectors where downtime can result in significant financial or safety risks.
Security levels and certification process
IEC 62443 defines multiple security levels (SL 1 to SL 4) based on threat sophistication and system criticality. Certification ensures that industrial networks meet stringent requirements for access control, data integrity, and incident response.
Adapting IEC 62443 to Industry 4.0 and IIoT environments
As Industry 4.0 technologies evolve, IEC 62443 provides guidance for integrating traditional operational technology (OT) with modern IT systems. Adopting this standard ensures IoT compliance requirements are met across industrial operations, enabling enterprises to protect both legacy and modern systems within a single, unified framework.
4.8. IEEE P2413 (Architectural Framework for IoT)
How IEEE P2413 provides a unified architecture for IoT systems
The IEEE P2413 standard offers a reference architecture that brings consistency to how IoT systems are designed and interconnected. It defines relationships between devices, networks, and applications, making large-scale IoT deployments easier to manage securely.
Security layer integration in complex IoT networks
IEEE P2413 emphasizes the inclusion of a dedicated security layer within the IoT architecture—covering device identity management, secure communication, and data governance. This structured design helps enterprises integrate Zero Trust IoT Architecture seamlessly into their operations.
Adoption trends among global enterprises in 2026
By 2026, IEEE P2413 has been widely adopted in sectors like transportation, smart cities, and logistics. Its adaptability allows enterprises to align their IoT infrastructure with multiple other Enterprise IoT Security Standards, ensuring compatibility and long-term scalability.
In summary, the adoption of these IoT Security Frameworks isn’t just about compliance—it’s about creating trustworthy digital ecosystems where innovation and protection coexist. By aligning with these global standards, enterprises can secure their networks, strengthen customer trust, and ensure resilience in an era where connected systems power every part of business operations.
Regional IoT Security Regulations and Compliance

As IoT ecosystems expand globally, every region is developing unique IoT Security Frameworks to ensure safety, trust, and compliance. For enterprises operating across borders, understanding and aligning with regional IoT security regulations is no longer optional—it’s a strategic necessity. These regulations define how data is collected, processed, and protected, helping businesses maintain Cybersecurity Compliance for IoT while avoiding hefty penalties and reputational damage.
North America: U.S. IoT Cybersecurity Improvement Act Updates (2026 Version)
In 2026, the U.S. IoT Cybersecurity Improvement Act has evolved to address modern threats like AI-driven exploits, quantum computing risks, and firmware manipulation. The updated act mandates that all federal IoT devices meet stringent authentication, encryption, and software update standards. Enterprises dealing with government contracts or using connected devices in regulated industries must now adopt Zero Trust IoT Architecture principles — ensuring every device is verified continuously before access is granted.
Additionally, U.S. organizations are encouraged to follow NIST’s updated IoT Security Frameworks, which now emphasize supply chain transparency, vulnerability disclosure programs, and lifecycle security management.
Europe: GDPR+IoT and the EU Cyber Resilience Act
Europe remains at the forefront of privacy-centric regulations. The integration of GDPR with IoT policies ensures that all connected devices respect data minimization and user consent principles. The EU Cyber Resilience Act (CRA)—enforced in 2026—further tightens security requirements for IoT manufacturers and enterprises. It mandates continuous monitoring, mandatory patching, and detailed risk documentation.
Enterprises deploying IoT devices in Europe must now demonstrate Enterprise IoT Security guidelines compliance by ensuring device firmware, cloud connectivity, and user data are protected from end to end. Non-compliance can lead to severe fines and product recalls, making adherence to frameworks such as ENISA’s IoT Security Guidelines essential for market survival.
Asia-Pacific: India, Japan, and China’s Advancements
In India, the Digital Personal Data Protection (DPDP) Act now extends to IoT ecosystems, emphasizing user consent, anonymization, and cross-border data flow restrictions. Indian enterprises must align their IoT solutions with both IoT security compliance norms and data localization mandates.
Japan continues to refine its IoT Security Guidelines under the Information-technology Promotion Agency (IPA), focusing on interoperability and risk-based device management. Meanwhile, China’s Cybersecurity Law updates have made IoT manufacturers accountable for backdoor access, requiring certification under government-supervised frameworks. Together, these developments show Asia-Pacific’s growing adoption of Zero Trust security models for IoT, strengthening both national and enterprise resilience.
Middle East & Africa: Smart City Framework Adoption
In the Middle East and Africa, rapid digital transformation through smart city initiatives has driven governments to adopt global IoT Security Frameworks. Countries like the UAE and Saudi Arabia are integrating NIST, ISO/IEC 27400, and ETSI standards into local policy to protect critical infrastructure. Africa, meanwhile, is building foundational Enterprise IoT Security Standards to secure healthcare, agriculture, and fintech sectors.
Why Localization of Compliance Matters
While global frameworks offer a baseline, localization of compliance ensures enterprises remain legally secure and culturally aligned. Adapting to regional laws helps prevent data sovereignty conflicts and enhances trust among users and regulators. For multinational organizations, aligning with diverse standards—from GDPR to NIST—builds operational resilience and ensures IoT Security Frameworks are implemented effectively across all markets.
By staying updated on regional mandates and harmonizing them with global frameworks, enterprises can strengthen their cybersecurity posture, maintain compliance, and confidently scale their IoT deployments worldwide.
Building a Comprehensive IoT Security Strategy in 2026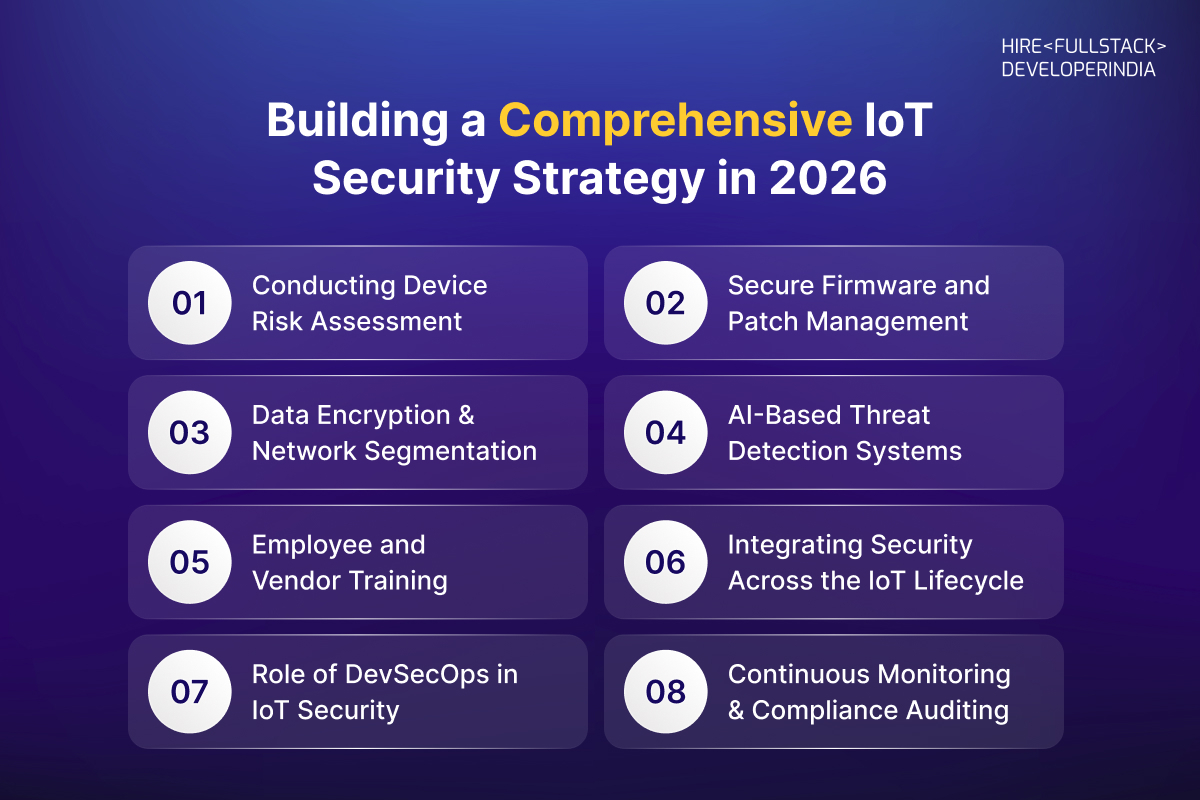
In 2026, enterprises can no longer afford to treat IoT security as an afterthought. With billions of connected devices interacting across global networks, a robust and proactive approach is vital. Building a comprehensive IoT security strategy requires organizations to align with globally recognized IoT Security Frameworks 2026 and implement Enterprise IoT Security Standards that ensure every device, user, and system remains protected throughout its lifecycle.
1. Conducting Device Risk Assessment
The foundation of any effective IoT security strategy begins with understanding device-level risks. Enterprises must categorize devices based on their data sensitivity, connectivity level, and exposure to external threats. This allows teams to apply appropriate controls guided by Cybersecurity Compliance for IoT frameworks such as NIST or ISO/IEC 27400. Identifying weak devices early helps prevent vulnerabilities that attackers might exploit later.
2. Secure Firmware and Patch Management
Firmware is the most common entry point for IoT breaches. To mitigate this, organizations should enforce secure firmware update mechanisms and automated patch management processes. Frameworks under IoT Security Frameworks 2026 emphasize digitally signed updates and rollback protection to prevent tampering. Regular patching not only safeguards against new vulnerabilities but also keeps enterprises compliant with evolving security standards.
3. Data Encryption and Network Segmentation
Strong encryption protocols remain essential for safeguarding IoT data during transmission and storage. Equally important is network segmentation, where critical devices operate in isolated zones to limit the blast radius of an attack. By segmenting IoT networks and enforcing access controls based on Zero Trust IoT Architecture, enterprises can ensure that only verified users and devices communicate within their ecosystems.
4. AI-Based Threat Detection Systems
With cyber threats becoming more sophisticated, traditional firewalls and antivirus tools are no longer enough. AI-driven monitoring and anomaly detection systems are now a key part of Enterprise IoT Security Standards. These tools can identify irregular device behaviors in real-time and automatically initiate containment measures, significantly reducing response time and potential damage.
5. Employee and Vendor Training
Human error remains one of the biggest security risks. Regular training ensures that employees and vendors understand secure handling of IoT devices, password hygiene, and the importance of compliance. Incorporating Cybersecurity Compliance for IoT awareness into workplace culture helps create a unified defense strategy across the organization.
6. Integrating Security Across the IoT Lifecycle
Security must be embedded from the very beginning—during the design, deployment, maintenance, and decommissioning stages. Embedding secure coding practices and performing vulnerability testing at each stage ensures long-term protection. This aligns perfectly with IoT Security Frameworks 2026, which promote “security-by-design” principles.
7. Role of DevSecOps in IoT Security
The DevSecOps model integrates security into every phase of development. For IoT systems, this means automating compliance checks, vulnerability scans, and encryption testing within CI/CD pipelines. DevSecOps makes sure that new device firmware and applications are secure before deployment, following a Zero Trust approach for IoT.
8. Continuous Monitoring and Compliance Auditing
Finally, enterprises must adopt continuous monitoring systems that track device behavior, detect anomalies, and generate security audit trails. Regular compliance audits ensure alignment with IoT Security Frameworks 2026 and regional regulatory standards.
By combining advanced technologies, robust frameworks, and a culture of security-first thinking, enterprises can create a resilient and adaptive IoT ecosystem—one capable of defending against evolving cyber threats in 2026 and beyond.
Future of IoT Security: Trends and Innovations to Watch
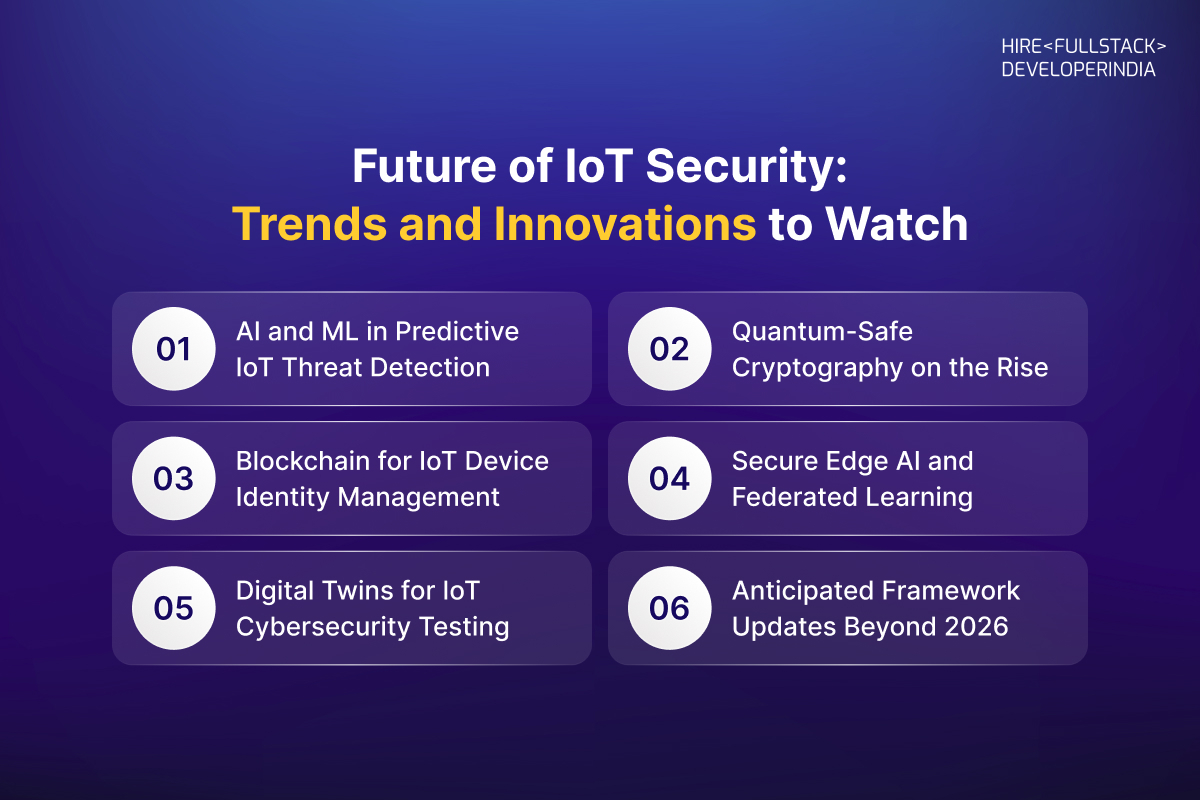
As enterprises continue to expand their connected ecosystems, the future of IoT security is shaping up to be more proactive, intelligent, and adaptive than ever before. The next phase of IoT Security Frameworks 2026 will emphasize predictive protection, decentralized control, and advanced cryptography — all working together to safeguard billions of interconnected devices. Here are the key innovations transforming the landscape of IoT security beyond 2026.
AI and ML in Predictive IoT Threat Detection
Artificial Intelligence (AI) and Machine Learning (ML) are becoming central to how enterprises prevent and respond to cyberattacks. Rather than waiting for an attack to occur, predictive AI models analyze behavioral patterns, network traffic, and device activities in real-time to identify anomalies. This proactive layer of defense enhances Cybersecurity Compliance for IoT by reducing detection time and automating responses. By 2026, more organizations are integrating AI-based analytics directly into Zero Trust IoT Architecture, ensuring that every device interaction is continuously verified.
Quantum-Safe Cryptography on the Rise
With quantum computing on the horizon, traditional encryption methods may soon become obsolete. Quantum-safe cryptography is emerging as a critical component of next-generation Enterprise IoT Security Standards. These algorithms are designed to withstand quantum-level decryption, providing long-term data security. Governments and enterprises are already testing post-quantum cryptographic standards to future-proof IoT communications and prevent large-scale data breaches in a post-quantum era.
Blockchain for IoT Device Identity Management
Managing the identity and authenticity of millions of IoT devices is one of the biggest challenges enterprises face. Blockchain offers a decentralized solution by creating immutable records of device identities, credentials, and transactions. This eliminates the risk of device spoofing or unauthorized access. Integrating blockchain with IoT Security Frameworks 2026 strengthens device-to-device trust and helps maintain tamper-proof audit trails across large networks.
Secure Edge AI and Federated Learning
Edge computing has shifted data processing closer to devices, but it also expands the attack surface. The next wave of innovation lies in Secure Edge AI — where AI models operate locally on edge devices with strong encryption and privacy-preserving mechanisms. Combined with federated learning, this approach enables collaborative model training without sharing raw data across networks. It enhances both privacy and scalability, aligning well with Zero Trust IoT Architecture principles.
Digital Twins for IoT Cybersecurity Testing
Digital twins — virtual replicas of physical systems — are being used for real-time IoT testing and threat simulation. Enterprises can replicate entire IoT environments to assess vulnerabilities before deploying devices into production. This trend supports compliance with Enterprise IoT Security Standards by allowing continuous validation and risk modeling without impacting real-world systems.
Anticipated Framework Updates Beyond 2026
Looking ahead, organizations can expect new standards and revisions in IoT Security Frameworks 2026, especially as AI governance, sustainability, and quantum security become major focus areas. Regulatory bodies like ISO, NIST, and ETSI are already developing guidelines that combine ethical AI use, environmental impact considerations, and adaptive cybersecurity measures.
In essence, the future of IoT security lies in intelligence, resilience, and continuous adaptation. Enterprises that proactively embrace these emerging technologies and align them with evolving IoT Security Frameworks will be better positioned to build secure, compliant, and future-ready connected ecosystems.
Challenges Enterprises Face in Implementing IoT Security Frameworks
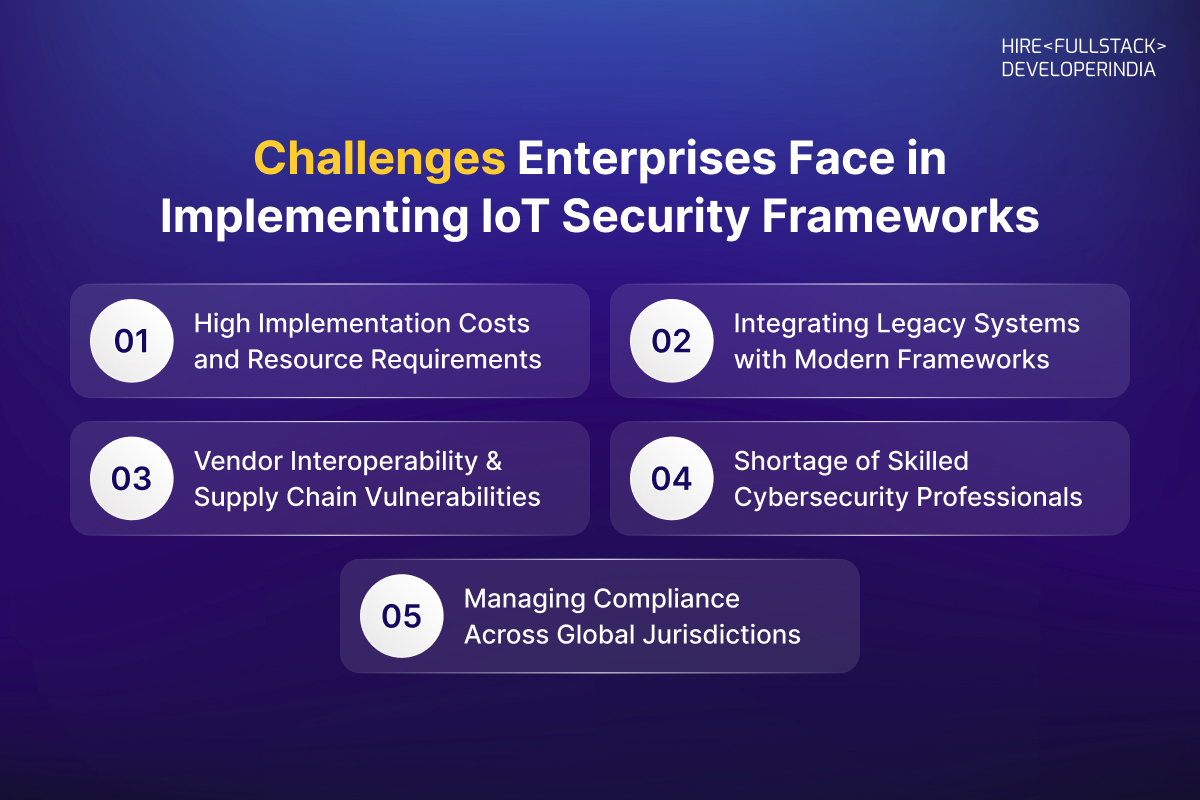
While IoT Security Frameworks 2026 offer a strong foundation for building safer and more resilient connected systems, enterprises often struggle to put these frameworks into practice. cost pressures to complex integrations, the journey toward full Cybersecurity Compliance for IoT is raFrom rely straightforward. Here are some of the key challenges organizations face when adopting and maintaining enterprise-grade IoT security measures.
1. High Implementation Costs and Resource Requirements
Establishing a secure IoT ecosystem demands significant investment — not just in technology, but also in time, infrastructure, and skilled personnel. Implementing Enterprise IoT Security Standards involves deploying encryption systems, continuous monitoring tools, and automated compliance checks. For many mid-sized businesses, these costs can become barriers to adoption, especially when balancing innovation with budget constraints.
2. Integrating Legacy Systems with Modern Frameworks
Many enterprises still operate on legacy systems that were never designed for modern IoT connectivity. Integrating these older platforms with IoT Security Frameworks 2026 introduces complexity, as outdated protocols may not support newer encryption or authentication methods. This mismatch often creates security gaps and increases exposure to cyber risks. To mitigate this, companies must adopt a phased modernization strategy while maintaining operational continuity.
3. Vendor Interoperability and Supply Chain Vulnerabilities
IoT ecosystems often rely on multiple vendors for hardware, software, and cloud integration. Each vendor may follow different Enterprise IoT Security Standards, making interoperability and data consistency difficult. Moreover, supply chain risks — such as tampered firmware or compromised third-party components — can undermine even the strongest Zero Trust IoT Architecture. Establishing strict vendor audits, certification checks, and end-to-end visibility is now essential for minimizing these risks.
4. Shortage of Skilled Cybersecurity Professionals
The growing demand for IoT security expertise far outpaces supply. Many enterprises struggle to find professionals trained in specialized areas such as embedded system security, network forensics, and compliance auditing. Without adequate human capital, implementing Cybersecurity Compliance for IoT becomes a challenge, slowing down overall digital transformation.
5. Managing Compliance Across Global Jurisdictions
Enterprises operating across regions face another hurdle — varying regulations and data protection laws. For instance, what meets compliance in Europe under GDPR might differ in Asia or North America. Aligning with multiple local and global IoT Security Frameworks 2026 adds administrative overhead and increases the need for tailored compliance strategies.
In short, while IoT frameworks are critical for securing enterprise operations, success depends on balancing technology adoption with realistic planning, skilled teams, and strong governance.
Best Practices for Ensuring Compliance and Robust IoT Security

Implementing IoT Security Frameworks 2026 is only the beginning — maintaining compliance and resilience requires continuous attention and disciplined practices. As connected ecosystems grow more complex, enterprises must follow a proactive approach to ensure their devices, networks, and data remain protected. Below are essential best practices that help organizations strengthen their IoT security posture while aligning with Enterprise IoT Security Standards.
1. Conduct Regular Audits and Penetration Tests
Routine security audits and penetration testing are crucial for identifying vulnerabilities before attackers do. Enterprises should perform internal assessments and engage third-party experts to validate Cybersecurity Compliance for IoT. Regular audits ensure that devices, firmware, and communication protocols meet global IoT Security Frameworks 2026 standards. This not only enhances security but also prepares businesses for regulatory reviews and certifications.
2. Adopt Zero Trust Principles
The Zero Trust IoT Architecture philosophy — “never trust, always verify” — is now a cornerstone of modern IoT protection. Every device, user, and network interaction must be authenticated and continuously monitored. By segmenting networks, limiting access privileges, and enforcing multi-factor authentication, enterprises can drastically reduce the impact of potential breaches. Integrating Zero Trust into IoT systems aligns perfectly with compliance frameworks like NIST and ISO/IEC 27030.
3. Keep Firmware and Software Updated
Unpatched vulnerabilities are one of the easiest ways for attackers to compromise IoT devices. Maintaining a strict firmware and software update schedule ensures all systems remain protected against the latest threats. Enterprise IoT Security Standards emphasize secure update mechanisms — including digitally signed patches and over-the-air updates — to ensure integrity during the process.
4. Maintain Transparency in IoT Data Handling
Data collected through IoT devices often includes sensitive personal or operational information. To build user trust and meet Cybersecurity Compliance for IoT regulations, organizations must clearly define how data is collected, processed, and shared. Transparency not only strengthens compliance but also minimizes legal risks under global privacy laws such as GDPR and the DPDP Act.
5. Collaborate with Certified IoT Security Partners
Given the fast-changing security landscape, partnering with certified experts can help enterprises stay ahead. IoT security consultants and solution providers familiar with IoT Security Frameworks 2026 can guide compliance implementation, risk assessment, and architecture design. Collaborations like these ensure that best practices are not just followed but tailored to each organization’s unique ecosystem.
By embedding these best practices into their operations, enterprises can build a resilient, compliant, and future-ready IoT environment — one that stands strong against evolving digital threats in 2026 and beyond.
Conclusion
In 2026, IoT has become a core part of how enterprises operate, connecting devices, systems, and data like never before. With this growth comes increased responsibility—IoT security is no longer optional. A single weak link in a connected network can expose sensitive data, disrupt operations, and harm business reputation. That’s why following IoT Security Frameworks 2026 is essential for every enterprise looking to protect its assets and maintain trust.
Adopting a combination of global frameworks and standards helps organizations create a strong and consistent security foundation. Guidelines from ISO/IEC, NIST, ETSI, and IoTSF provide practical measures for device management, data protection, and network security. Aligning with Enterprise IoT Security Standards ensures that all devices follow the same secure practices, while Cybersecurity Compliance for IoT helps enterprises meet legal and regulatory requirements across regions. Principles such as Zero Trust IoT Architecture further strengthen defenses by verifying every device and user interaction, reducing the chances of unauthorized access.
The key to lasting security is being proactive. Regular audits, firmware updates, AI-based monitoring, and employee training help enterprises stay ahead of threats rather than simply reacting to incidents. Integrating security throughout the IoT lifecycle—from design to decommissioning—creates a resilient system that can grow with the business.
Ultimately, building a secure and compliant IoT ecosystem in 2026 is about combining the right frameworks, technologies, and practices. Enterprises that take this approach can not only protect their operations but also leverage IoT to its fullest potential, confidently scaling their connected networks for the future. Security, consistency, and compliance are no longer just technical requirements—they are essential pillars for enterprise success in the IoT era.
Don’t wait for a security breach to act. Contact Us! to learn how our team can help protect your IoT network with the latest frameworks and best practices.
.jpg?w=1920&q=75)

